
Israeli domain registration server hacked
Gaza offensive prompts Islamic group Team Evil to 'hijack' Israeli domain names by hacking into registration server, rerouting users of Ynetnews, Bank Discount to hostile webpage. Original sites were not hacked
An Islamic group based on Morocco hacked into DomainTheNet's registration system server on Friday, effectively "highjacking" various prominent domain names, the likes of ynetnews.com and Bank Discount, and rerouting users to a page featuring anti-Israel messages
DomainTheNet is a multinational registration service provider (RSP), which offers registration and site-hosting services. The attack is believed to be in retaliation to Operation Cast Lead in the Gaza Strip.
The attack resulted in some users being referred to the hostile webpage, while others were able to access the original websites, undisturbed. The group did not hack the actual websites.
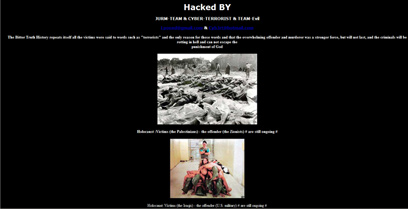
The hostile webpage
Appearing as a defacement attempt at first, the attack soon turned out to be more sophisticated: The hackers were able to obtain a password which granted them access to the server which updates and "translates" the websites' IP addresses into a Domain Name Service; and change the IP's numeral values, effectively rerouting users away from the original websites.
The attack was claimed by a Moroccan group calling itself "Team Evil," which had previously hacked other Israeli brands such as Cellcom, Shilav and BlueSquare. Ynet has learned that the server hosting the hackers' website is based in Japan.
Ynet's Editor in Chief Jon Feder, said that "the fact that hackers were able to breach DomainTheNet, by allegedly using valid client passwords, is highly disturbing.
"Ynet is looking into all aspects of the incident, be they technical, procedural or legal vis-à-vis the domain registration service and the matter will be dealt with without delay."
Yoav Keren, CEO of DomainTheNet Technologies, told Ynet that the hackers were able to track passwords used by the online customer services system, to access the domain management system, posing as system administrators authorized to change IP addresses.
DomainTheNet's staff spotted the security breach, blocked it and thwarted further attempts by Team Evil to make any further changes.
The updating of all DNS servers around the world may take 24 hours or longer, resulting in some users still being rerouted to the hostile webpage.
The site formed by the group featured graphic images of dead bodies and abused Iraqi prisoners.
The message, featured alongside a propaganda song in Arabic, read "The Bitter Truth History repeats itself all the victims were said to words such as "terrorists" and the only reason for those words and that the overwhelming offender and murderer was a stronger force, but will not last, and the criminals will be rotting in hell and can not escape the punishment of God"
Ynet has learned that the server hosting the hackers' website is based in Japan. The attack was claimed by a Moroccan group calling itself "Team Evil," which had previously hacked other Israeli brands the likes of Cellcom, Shilav and BlueSquare.










