New virus targets Iranian computers
Iranians announce new 'targeted attack' after detecting malware that deletes entire user files, wipes data on certain dates
An advisory issued by Iranian authorities described the new threat as a "targeted attack," but said that it has a simple design and is not similar to other sophisticated targeted attacks previously seen in the region.
Related stories:
- Up in Flames? Not necessarily
- Computer virus briefly hits Iran’s oil industry
- Report: Flame virus gets order to self destruct
Despite its simplicity in design, the malware is efficient and can wipe disk partitions and user profile directories without being recognized by anti-virus software," the Maher Computer Emergency Response Team Coordination Center said in an its advisory.
According to the Computer World website, the malware is designed to delete all data from disk partitions identified with letters D to I, as well as files located on the desktop of the currently logged in user, security researchers from antivirus vendor Symantec said Monday in a blog post.
- For more on the raging cyber war click here
The malware initiates its data wiping routine on certain dates, the next one being Jan. 21 2013. However, the dates of Oct. 12, Nov. 12 and Dec. 12, 2012, were also found in the malware's configuration, suggesting that it may have been in distribution for at least two months.
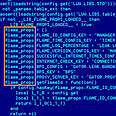
The Maher Center said the malware's installer, also known as the dropper, is called GrooveMonitor.exe.
That filename was likely chosen as a disguise because it is normally associated with a legitimate Microsoft Office 2007 document collaboration feature called Microsoft Office Groove.
According to Computer World, it is unclear clear how the malware is being distributed but experts are not ruling out the possibility that an internal actor is uploading it to network shares.
- Receive Ynetnews updates directly to your desktop










