Microsoft partly blames US government for cyberattack
After more than 150 countries were hit by malicious software programs on Friday due to a loophole in Microsoft's security measures, top Microsoft lawyer Brad Smith says that it is also upon countries to update their security systems, instead of 'stockpiling' code that can later be used by hackers looking to cause harm.
Microsoft's top lawyer Brad Smith is laying some of the blame for Friday's massive cyberattack at the feet of the US government.
Smith criticized US intelligence agencies, including the CIA and National Security Agency, for "stockpiling" software code that can be used by hackers. Cybersecurity experts said the unknown hackers who launched this weekend's "ransomware" attacks used a vulnerability that was exposed in NSA documents leaked online.
In a post on Microsoft's blog, Smith said: "An equivalent scenario with conventional weapons would be the US military having some of its Tomahawk missiles stolen."
"Clearly, responding to this attack and helping those affected needs to be our most immediate priority," wrote Smith. "At the same time, it’s already apparent that there will be broader and important lessons from the “WannaCrypt” attack we’ll need to consider to avoid these types of attacks in the future."
Smith added that "this attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem. This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the US military having some of its Tomahawk missiles stolen. And this most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cybersecurity threats in the world today—nation-state action and organized criminal action.
"The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world. We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits."
UK and Europol warn of of additional cyberattacks in the near future
Meanwhile, Britain's National Cyber Security Center has joined others in warning that more cases of "ransomware" attacks may come to light as a new work week starts Monday.
The organization predicted that the problem could be "at a significant scale" because some infected machines have not yet been detected, and existing infections can spread within networks.
It said Sunday that a similar cyberattack could also recur, though it did not have "specific evidence" of this.
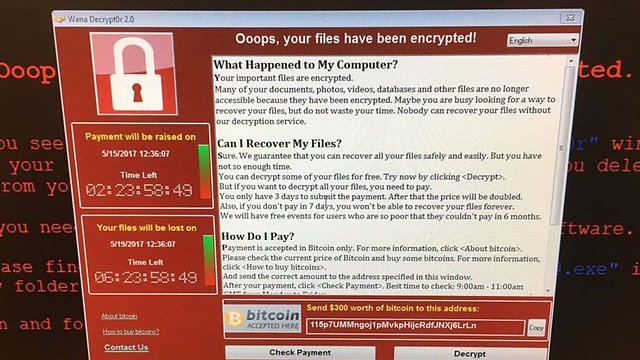
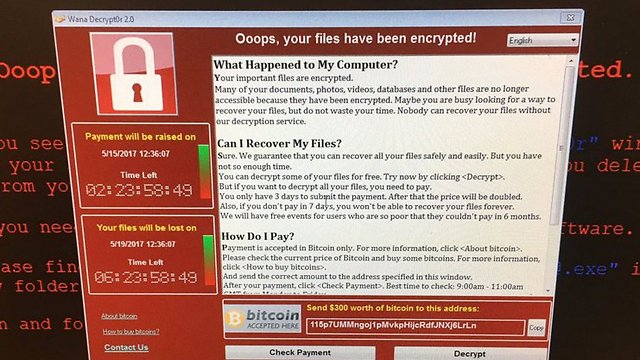
The warning echoed a statement by Europol, Europe's policing agency, earlier Sunday. Europol said the malware has claimed some 200,000 victims across 150 countries and that numbers are still going up. Officials urged organizations and companies to immediately update their security software.
An executive at a cybersecurity firm that helped block a global ransomware attack name Ryan Kalember additionally stated that new variations of the malicious worm are circulating and researchers expect one to develop that can't be stopped.
Kalember, who is a senior vice president at Proofpoint Inc., said that millions of devices could be vulnerable if they haven't applied security patches over the weekend.
Kalember stressed that if a new variant without a so-called kill switch pops up, then organizations will be on their own to prevent it from taking over their computers.
Proofpoint and a British cybersecurity researcher teamed up Friday to derail the attack that was said to strike at least 100,000 organizations in 150 countries.
It is believed to be the biggest online extortion ever, hitting British hospitals, German rail and companies and government agencies.