Iranian hackers launch virtual honeypot scheme
Iranian hacker group Cobalt Gypsy creates fake profile of beautiful, London-educated photography enthusiast named Mia Ash to hack employees in security-sensitive Middle Eastern companies to steal sensitive information.
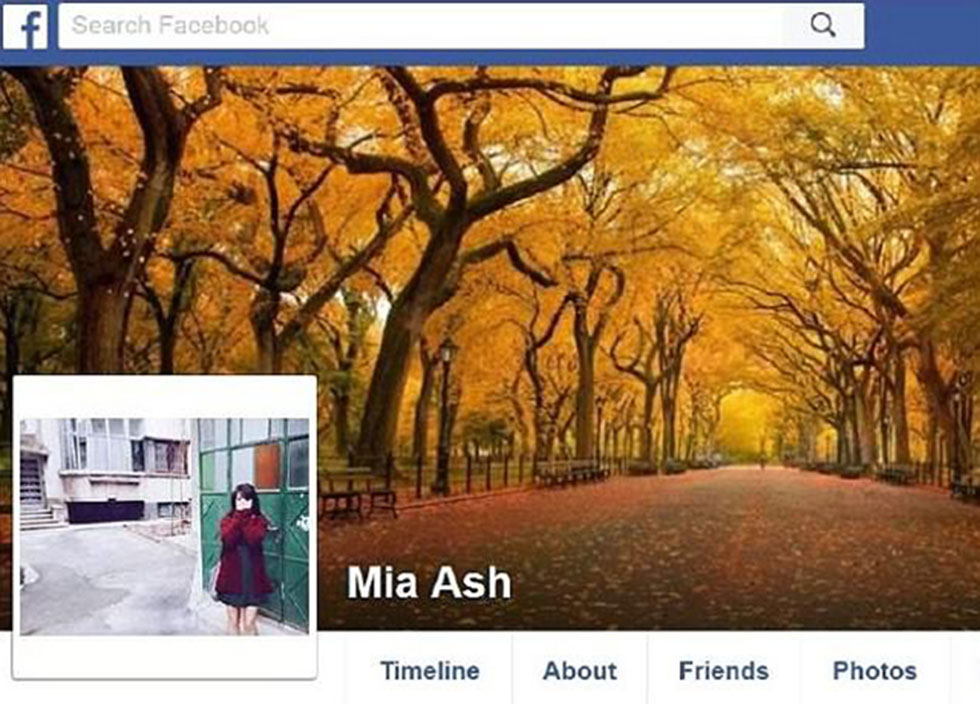
Mia Ash is a 29-year-old independent photographer and an attractive woman living in London who loves listening to indie music and "surfing on social media." She's been studying at the University of London and is a bit of a hipster—and she's looking for love. Oddly enough, she seems to be attracted mainly to older men in senior positions in the energy, aviation and information technology industries.
There is only one problem—Mia Ash doesn't exist. In fact, her profile is fake, designed to steal secret information.
The investigators who uncovered the plot believe Mia was created by hackers linked to Iran. According to media reports, the scheme was partially successful and senior executives in sensitive industries in Israel, the United States, India and Saudi Arabia may have exposed confidential information to the same fake profile.
Mia also installed spyware on the computers of the companies from which it gathered information before it was discovered last February.
In the same month, a Middle East company whose name has not been revealed was approached by the US security company SecureWorks to investigate the espionage attempt.
An unnamed employee was flattered when Mia approached him on LinkedIn with questions related to photography—a passion they share. Within a short time they became friends on Facebook, where they corresponded and talked about work and hobbies.
Mia's Facebook, Instagram, LinkedIn and Blogger accounts have shown that many of her friends are photographers and that her relationship status is defined as "It's Complicated."
One day, she asked her new friend if he could do her a favor. She asked him for feedback on a photograph, which included downloading and filling out an Excel sheet. She claimed that this should be done on his work computer, otherwise technological problems would arise. The employee swallowed the bait and as soon as he downloaded the files, he introduced spyware into the system.
Fortunately, the company's cyber security detected this.
The investigation found that Mia's profile had been created a year ago, and that those responsible for it had forged contacts with real photographers over the course of months to give the fictional character credibility. Mia's photos were taken from the profile of a Romanian student.
An Australian newspaper reported that investigators believe the profile was created by the "Cobalt Gypsy" hacker group, which is believed to be backed by Iran. The same group was linked to cyber attacks in the past that compromised thousands of computers in Saudi Arabia and cyber attacks on Israeli companies.
This is, of course, not the first case of a fictitious Facebook profile created for espionage purposes.
Six months ago, the IDF said that Hamas had stepped up its cyber espionage activity aimed at IDF soldiers in order to gather intelligence about the army's operations and its deployment on the Gaza border.
Hamas operatives would pose as attractive, young Israeli women by assuming their identities and making contact with soldiers, mainly through Facebook. Following contact with soldiers, the Hamas operatives would attempt to engage in an intimate virtual relationship and convince soldiers to download an "application" that would allow for video chatting.
The "application" was a Trojan horse, which gave Hamas total control over the device and allowed the terrorist organization to activate the camera and microphone, access contacts, videos and photos, and even Whatsapp conversations and emails—all without the soldier being aware.
Moreover, Hamas also managed to delete the application from the devices, while simultaneously installing more sophisticated monitoring and control applications without leaving a trace.