Iranian hackers managed to penetrate the networks of about 32 Israeli companies, the a information security company ESET announced Monday. The hackers also penetrated a company in Brazil and another in the United Arab Emirates. The names of the companies were not disclosed, but according to what is known they operate in diverse fields,including insurance, medicine, industry, communications, IT, technology, retail, automobile, law, financial services, architecture and civil engineering.
Read more:
The group behind the campaign has been identified Ballistic Bobcat, which is known by other names including Charming Kitten, TA543 or PHOSPHORUS as well as APT35/42. The group's main goal is cyber espionage, but it also operates on other levels such as data theft or ransom attacks. Moreover, according to the findings, the group was not the only party that managed to gain access to the victims' networks. At least 16 companies were affected by secondary attackers, although ESET did not specify which ones.
2 View gallery


More than 30 Israeli companies have come uner cyberattack
(Photos: Generated image - AP, Shutterstock)
"Users are advised to install up-to-date security patches on every device exposed to the Internet and to be alert for new applications that appear unexpectedly in their organization," said Adam Berger, an ESET researcher who uncovered the backdoor known as Sponsor and analyzed the group's latest cyber attack campaign. The Sponsor backdoor uses configuration files stored on a computer hard drive. The files are secretly run as batch files, and created to look legitimate, to avoid detection by security scans.
The Ballistic Bobcat group began operating the backdoor in September 2021. During the coronavirus epidemic, the Ballistic Bobcat group attacked organizations related to the pandemic, including the World Health Organization (WHO) and medical researchers. It is suspected that the attacks were intended to convey information to the Iranian authorities regarding dealing with the disease worldwide and the vaccines that were developed at the time.
The researchers also found that the hackers took advantage of a well-known weakness in Microsoft's Exchange email servers in at least 23 of the 34 attack cases. A software update for this vulnerability has already been released by Microsoft so the chances are that the victims did not update their systems in real time, which allowed the hackers to penetrate.
2 View gallery
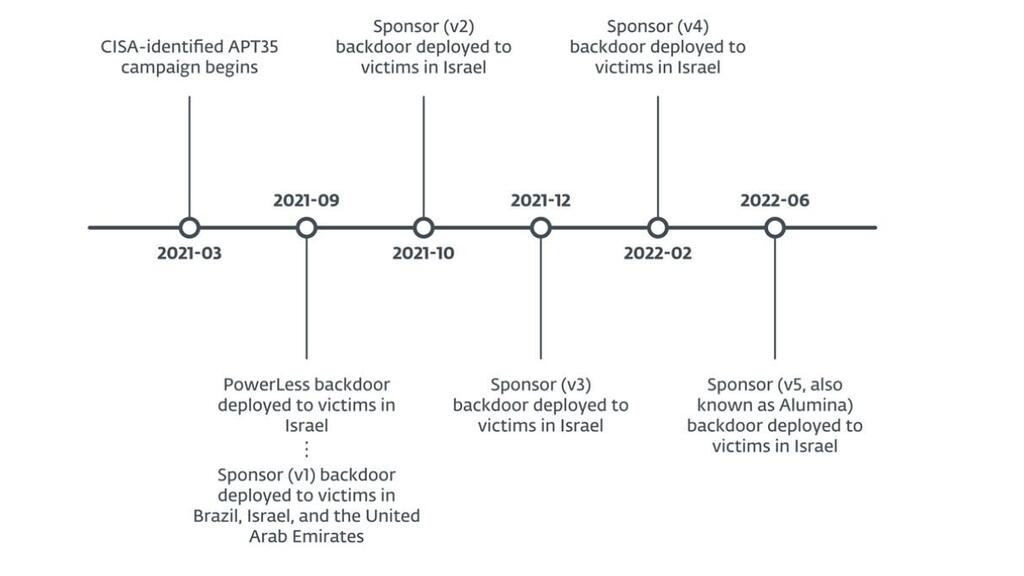

Diagram of the Iranian cyber campaign that attacked companies in Israel
(Screenshot: ESET Research)
The hacks were not a targeted campaign, according to researchers. The hackers did not proactively seek to break into the specific companies, but simply scanned with the help of hacking tools and when they found ways in simply used them to penetrate the companies' networks.
Iranian hacking groups regularly operate against targets in Israel. At any time there are a large number of attempts to identify weak points in corporate, government and military networks and exploit them. Russian, North Korean, Syrian and Turkish attack groups also operate regularly in Israel, although their purpose is usually more criminal than political-strategic. However, there is no doubt that a group that manages to successfully penetrate computers in Israel may leverage the operation at the political level as well.
For several years Israel and Iran have been running systematic cyberattacks under the radar. The activity of the Iranians has been identified in several cases such as the shutdown of the Hillel Yaffe hospital or intrusion into the networks of defense companies, municipalities or even national infrastructures and government companies. In some cases it is about gathering intelligence, in other cases the goal is to embarrass and shut down an activity or plant trojan programs for future use. At this stage it is not clear whether the identified campaign succeeded in its goals or whether it is still actively affecting other victims.

