An international law enforcement operation led by Britain's National Crime Agency and the FBI has arrested and indicted members of the Lockbit ransomware gang, in an unprecedented police operation that has struck one of the world's most notorious cybercrime gangs. The United States has charged two Russian nationals with deploying Lockbit ransomware against companies and groups around the world. Police in Poland and Ukraine made two arrests.
Read more:
The NCA, U.S. Department of Justice, FBI and Europol gathered in London to announce the disruption of the gang, which has targeted over 2,000 victims worldwide, received more than $120 million in ransom payments and demanded hundreds of millions of dollars, the DOJ said.
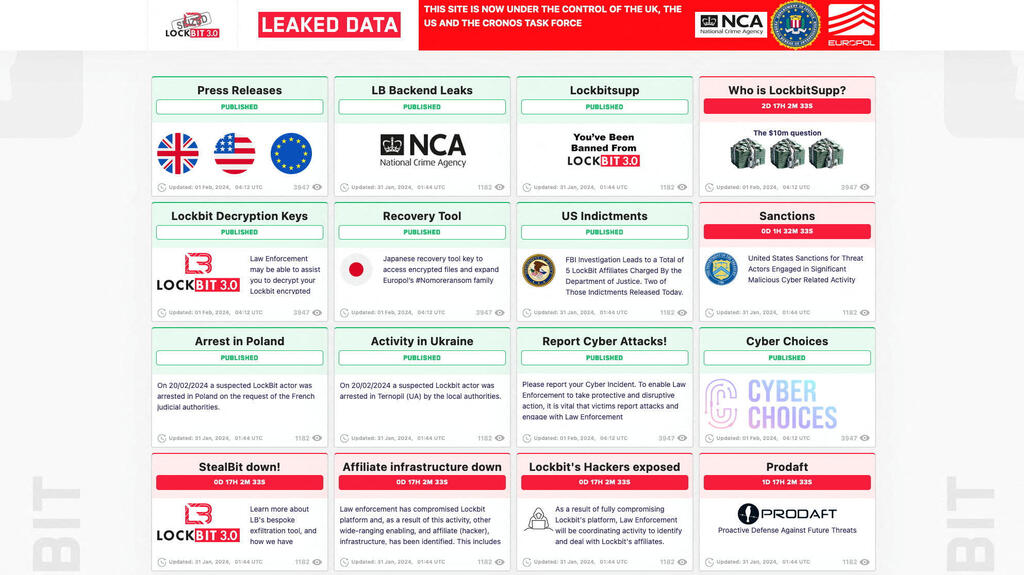
Britain's National Crime Agency Cyber Division, with the U.S. Department of Justice, the FBI and other law enforcement agencies seized control of websites used by Lockbit the gang and U.S. and British authorities said. The agencies also took the extraordinary step of using Lockbit's own website to release internal data about the group itself.
"We have hacked the hackers," Graeme Biggar, director general of the National Crime Agency, told journalists. "We have taken control of their infrastructure, seized their source code and obtained keys that will help victims decrypt their systems,"
The takedown, dubbed "Operation Cronos" was an international coalition of 10 countries, he said. "Together, we have arrested, indicted or sanctioned some of the perpetrators and we have gained unprecedented and comprehensive access to Lockbit's systems".
A representative for Lockbit did not respond to messages from Reuters seeking comment.
Obtained in New Jersey, the unsealed indictment charges Artur Sungatov and Ivan Kondratyev, also known as Bassterlord, with using Lockbit ransomware to target victims in manufacturing, logistics, insurance and other companies in five states and Puerto Rico, as well as in semiconductor and other industries around the world. Additional criminal charges against Kondratyev were unsealed on Tuesday related to his use of ransomware in 2020 against a victim in California, the Justice department said.
Both men were also sanctioned by the U.S. Treasury.
2 View gallery

darkweb site called Lockbit appears after law enforcement agencies took control of it
(Photo: Reuters)
This criminal group works with a unique business model in the cyber world of freelances using attack tools developed by the group and sharing in the profits when their attacks are successful and the victims pay the ransom," Israel's Cyber authorities said adding many in Israel have chosen to pay the sum demanded by their attackers.
The authority said there has been an increase in cases reported in recent months that are confirmed to be by the Lockbit technology, although they do not seem to be connected to the war in Gaza. A new manual outlining the tactics used and the ways to defend against them was published on Tuesday.
Many of the attacks were made on users connecting remotely to their systems or via VPNs.
In November last year, Lockbit published internal data from Boeing, one of the world's largest defense and space contractors, and said the U.S. arm of China's ICBC had paid a ransom following an attack that disrupted trades in the U.S. Treasury market. In early 2023, Britain's Royal Mail faced severe disruption after an attack by the group.
Lockbit caused billions in damages
Ransomware is malicious software that encrypts data; Lockbit and its affiliates makes money by coercing its targets into paying ransom to decrypt or unlock that data with a digital key. The gang's digital extortion tools have been used against some of the world's largest organizations in recent months.
Its affiliates are like-minded criminal groups that Lockbit recruits to wage attacks using those tools. Those affiliates carry out the attacks, and provide Lockbit a cut of the ransom, which is usually demanded in the form of cryptocurrency, making it harder to trace.
Operation Cronos seized 34 of Lockbit's servers, arrested two members of the gang, froze 200 cryptocurrency accounts, and closed 14,000 "rouge accounts" used online to launch Lockbit's operations, the police agencies said.
Lockbit has caused monetary losses totaling billions, the NCA's Biggar said, to businesses who not only had to pay ransom payments, but also had to shoulder the cost of getting their systems back online.
Before it was taken down, Lockbit's website displayed an ever-growing gallery of victim organizations that was updated nearly daily. Next to their names were digital clocks that showed the number of days left to the deadline given to each organization to provide ransom payment.
On Tuesday, the Lockbit leak website had been transformed by the NCA, FBI and Europol into a leak site about the criminal gang itself, onto which international police agencies published internal data from inside the group, and countdown clocks threatening to reveal upcoming sanctions and the identity of Lockbit's ringleader, "LockbitSupp."


