A Russian online influence campaign is spreading fake articles to generate disinformation and confusion online according to researchers from the Israeli cybersecurity company, Cybereason which says they may be trying to alter public opinion or even incite conflict and obscure the truth.
Read more:
"We have uncovered a disinformation infrastructure linked to the Russian government in Israel, designed to influence decision-making in Jerusalem by imitating reputable Israeli news sites, Ilan Sokol, Cybereason CEO, said. "This campaign involved creating imposter websites that closely resembled legitimate and prominent news outlets. For example, they produced an internet site that mimicked and matched the distribution and content of genuine news sites, intending to confuse users and make them believe they were accessing the real site through a similar web address," he said.
"One example of the fake content published includes an article praising Israel's ambassador to Ukraine for allegedly giving an interview to a local news outlet. These false articles continue to echo old Russian narratives, accusing Ukrainian authorities of being Nazis who continue the work of the German Reich. Another false article accused U.S. President Joe Biden of orchestrating protests and attempting to topple the Israeli government. This suggests that the Russian government is attempting to sow discord between Jerusalem and Washington."
3 View gallery
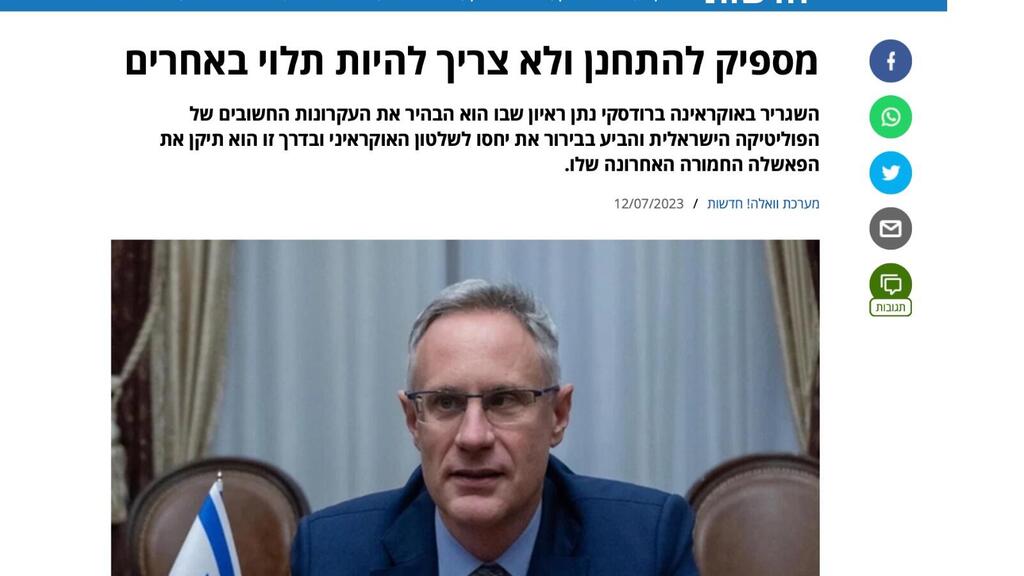

A fake site with an article about Israel's Ambassador to Ukraine support of Russia
(Photo: Cybereason)
Cybereason researchers investigated and identified the location from which the hackers were operating, and it appears to be within Russia itself. While the fake website's address did not reveal the location, through cross-referencing with similar domains, the researchers inferred that the campaign originated in Russia. According to data from Similarweb, the site received around 1,000 visits since its creation about eight days ago.
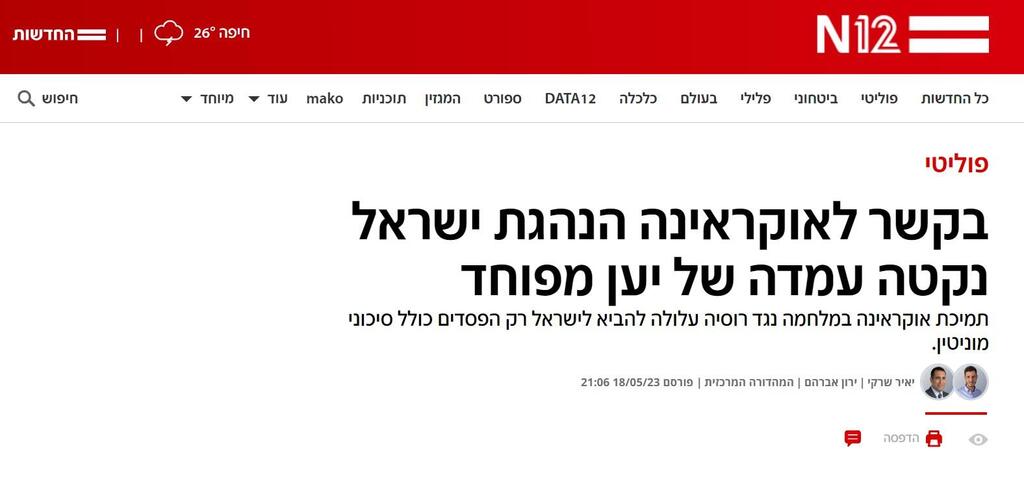
Cybereason researchers also discovered additional examples of impersonation targeting other media outlets, such as the "Mako" and N12 websites, both belonging to the Keshet Group. Several articles on the fake site, posing as the official N12 site, attempt to portray Ukraine as an instigator of conflict in the Middle East. These articles attribute statements to real and credible journalists who have no association with the content published under their names. Furthermore, the articles quote supposed government officials warning against Ukraine, statements that were never made.