The Imperva cybersecurity company uncovered one of the most impressive phishing campaigns ever seen. Company investigators found that a gang of Russian hackers was behind phishing text messages sent to users worldwide, in 40 different languages. The purpose of the global effort was to steal financial information including credit card and bank account numbers by impersonating familiar websites or organizations that often receive payments online.
More stories:
In Israel for example, the Israel Postal Company often asks customers who receive packages from abroad to pay customs and administrative payments. Hackers send bogus messages to Israelis demanding such payments online while presenting themselves as the valid Postal Company website.
4 View gallery


A gang of Russian hackers was behind phishing text messages sent to users worldwide, in 40 different languages
(Photo: Shutterstock)
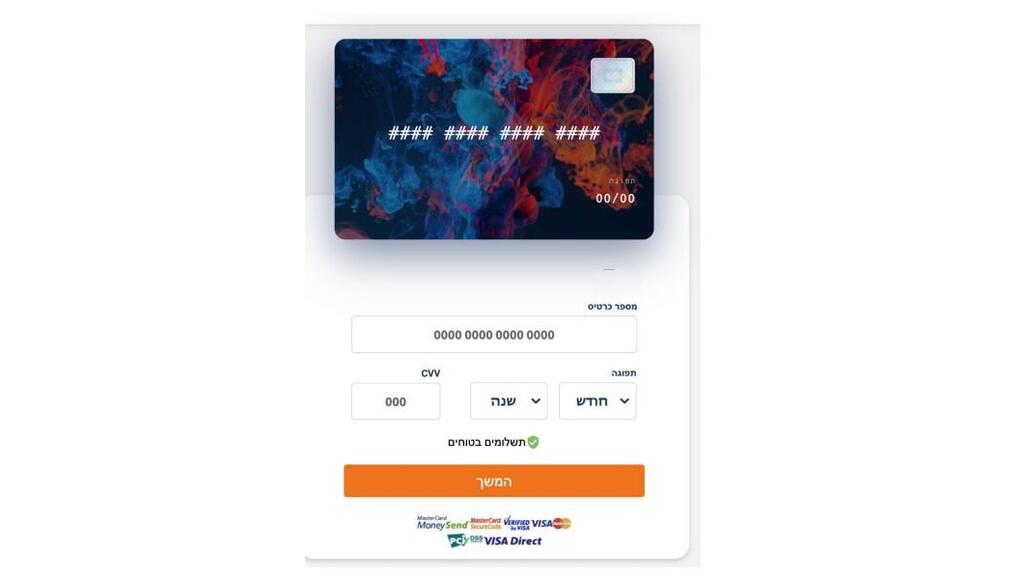
Their method is simple. They attach a link to pay or receive payment, and their victim clicks on it and is transferred to another page that seems identical to the real website where he or she is then asked to supply personal financial information. That information is then kept by the hackers. Investigators said they saw that when they supplied financial information, the hackers attempted to transfer the sum out of their account within minutes.
In this massive operation that began around May 2022, some 800 domain names are used – all nearly identical to valid websites. In all, the investigators identified 340 companies and brands whose sites were forged, among them Facebook, FedEx, DHL and Booking.com. They built a computerized ability to steal the design of websites on their forged pages in the required language and quickly promote them.
"This is a global phishing attack targeting some 340 companies on a daily basis. The hackers built a generic support infrastructure in 48 languages that allows them to easily add more targets for their attack," Imperva investigator Shlomit Yerushalmi said. "A big part of their strategy is to successfully imitate the user's experience, to avoid detection. They even provided live customer service operators. We found detailed evidence of this," she said.
Yerushalmi said the scope of the operation is unusual and she believes there are thousands of people who have fallen victim to it and have provided their financial information to the hackers.
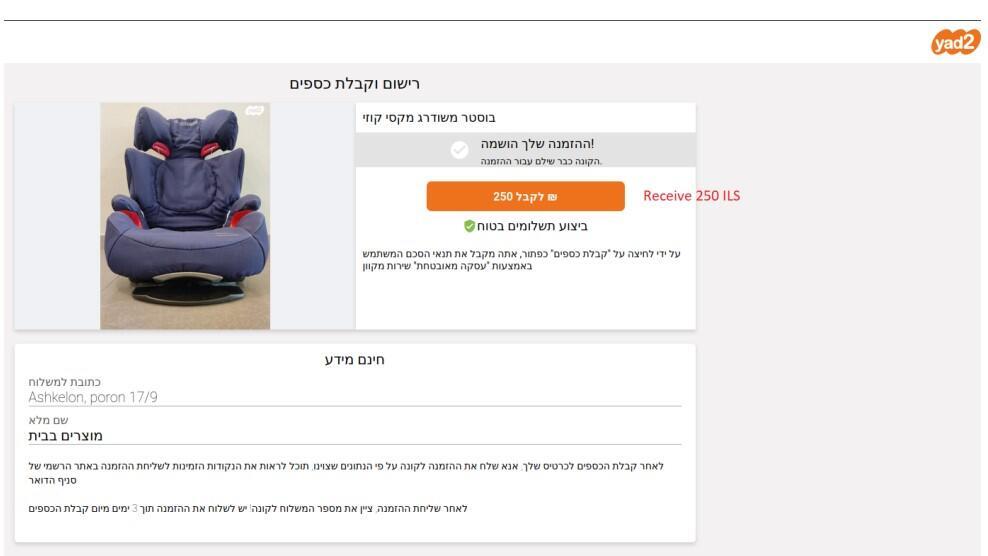
The scheme was detected when an employee of Imperva attempted to sell a used infant car seat on Yad2, a well-known Israeli website. He was contacted via WhatsApp by someone who claimed to be interested and who provided a link to what appeared to be a reputable site in order to make the payment. In the message, the Imperva staffer was told that all he had to do to receive his money was to click on the orange button at the center of the page. That sent him to another page where he was asked to fill in his credit details. To his surprise, the page even had a chat option with a customer service representative, that was available to help with completing the process - a real person, who would convince targets to provide the information, using any appropriate language.
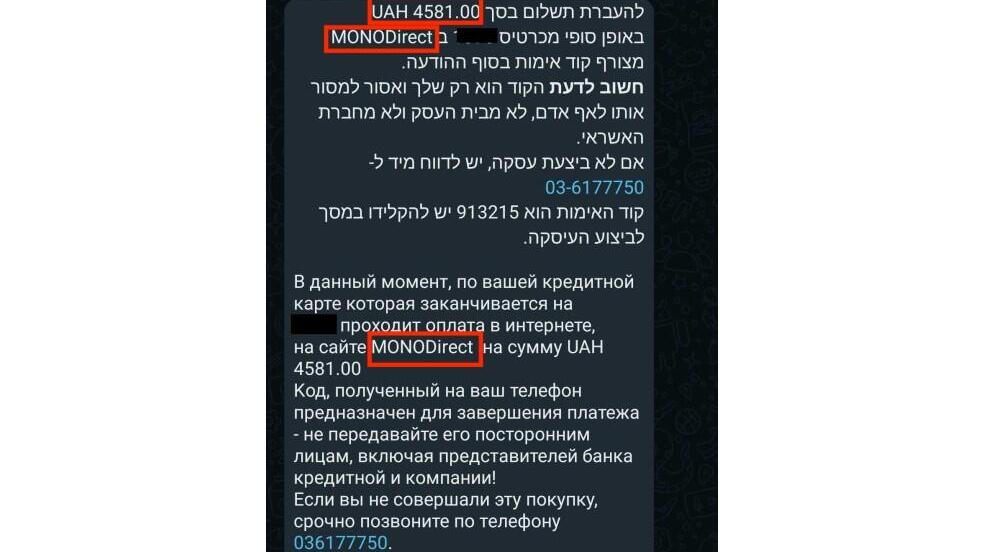
Once the information was provided, the Imperva employee received a text message from his credit card company, asking him to approve payment, as is standard procedure in place to prevent the use of stolen cards. The hackers then attempted to withdraw 4,500 Ukrainian hryvnia (the equivalent of 450 shekels or $122.) Had approval been granted, the money would have been transferred to the hackers.
Although a Ukrainian bank was used to launder the stolen money, the investigators said the campaign is Russian. "We found that the hackers mostly used a Russian code that operates fake websites," Yerushalmi said. "They also added insults often used against Ukrainians and the IP addresses were Russian," she said, adding that there could be an additional effort to disparage Ukraine in line with Russian propaganda, although no connection to official Russian political entities was found. "These are criminals who were out to steal money," she said.
Such cyber scams are not common. Most hackers concentrate on one brand and use one language. There are phishing operations that can be hired but investigators have not seen such abilities used by any one gang for its own operation. They may be trying to maximize their profits before others enter the game, knowing that if they provide their infrastructure to others it would quickly be detected.
This phishing operation proves how important it is to be alert and vigilant before interacting with any unknown entity online. "If there is doubt, there is no doubt," the investigators say should be the rule of thumb.